This month we examine some expert techniques for building more secure networks. Don't let intruders crash your dance. Moreover prevent that other end accept more packets. By manipulating packets, you can scan systems stealthily, generate traffic floods, and generally create packets to your heart's content. The scanning algorithm is still not optimal, but already quite fast. 
| Uploader: | Vudojind |
| Date Added: | 7 March 2010 |
| File Size: | 34.62 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 81616 |
| Price: | Free* [*Free Regsitration Required] |
hping2 package in Ubuntu
James UbbuntuAuthor s: Linux has a fantastic selection of firewalls for securing stand-alone computers or whole networks. Viewing a packet generated by hping in Wireshark.
UDP header tunable options are the following: If no interfaces match hping3 will try to use lo. The -S option sends a SYN packet, which often is used to create scans that are hard for intrusion detection systems to detect and flag as threatening. Many hosts ignore or discard this option. You can override the ttl of 1 using the --ttl option.
At the Hop » Linux Magazine
Several applications depend upon hping2, which has been around quite a bit longer than hping3. If you don't specify the data size hping will use the signature size as data size.
Are your borders protected? When packet is received sequence ubutnu can be computed as replies. A less obvious advantage of hping3 is that Salvatore Sanfilippo, the ubunfu of all things hping, rewrote much of the underlying code.
Keep your edge with these powerful Linux administration tools: To do this, you would issue the command shown with the accompanying output in Listing 1.
Default 'virtual mtu' is 16 bytes. The only real difference is that the standard hping behaviors are encapsulated into a scanning algorithm. As you can see target host's sequence numbers are predictable.
This month we examine some expert techniques for building more secure networks. Generating custom packets is nothing new. When it comes to penetration testing and security audits, hping is one of your best friends.
Hping2 - aldeid
Almost every wireless LAN has some potential security weaknesses. This seems a solaris problem, as stated in phing2 tcpdump-workers mailing list, so the libpcap can't do nothing to handle it properly. For example, to monitor how the 5th hop changes or how its RTT changes you can try hping3 host --traceroute --ttl 5 --tr-keep-ttl. Try hping3 host --traceroute.
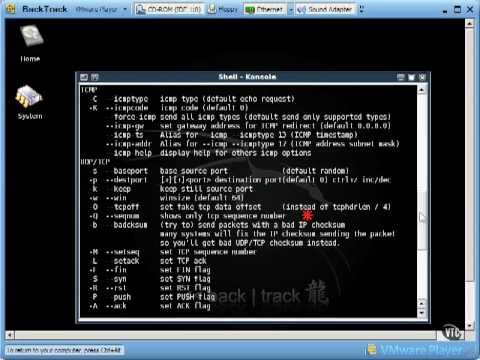
However replies will be sent to spoofed address, so you will can't see them. Suppose you want to send buuntu TCP packets to a system named jamesand you want those packets to hit port 80 on james. The scan mode uses a two-processes design, with shared memory for synchronization. We'll show you how to test your firewalls and intrusion detection systems with hping.
Category: Card
When this option is turned on, matching packets will be accept from all the destinations. If you use the command without any arguments, hping3 places you into a session, much like the old nslookup command.
Although you can use IPTables to set up a firewall, the configuration is often the most difficult step.
To install hping, enter the following command:. Increments aren't computed as id79564-id[N-1] but using packet loss compensation.

Over the years, hping has become the de facto packet generator. Hping provides a single, universal solution that helps prevent many problems of the previous generation. If you need that source port not be increased for each sent packet use the -k --keep option.

Комментариев нет:
Отправить комментарий